How can I host my Django website from Godaddy.com? I doubt if godaddy cpanel has this feature but if you can find modsec manager plugin in your cPanel,.
Sucuri should be filtering most bad traffic. I don\'t recommend whitelisting the IP completely, except maybe in csf.ignore if you are using CSF and LF_MODSEC. That\'s all I would do (add the ip to csf.ignore so it doesn\'t get blocked completely). Reson being, things like cloud firewall or ddos protection are forwarding requests that other people make; it could be forwarding malicious requests along with good ones.
Obviously the point of the sucuri firewall is to filter out the bad ones, but it might miss some. If there\'s one particular rule that the sucuri IP is tripping due to it proxying requests or something, you should just whitelist the rule(s) causing issues.

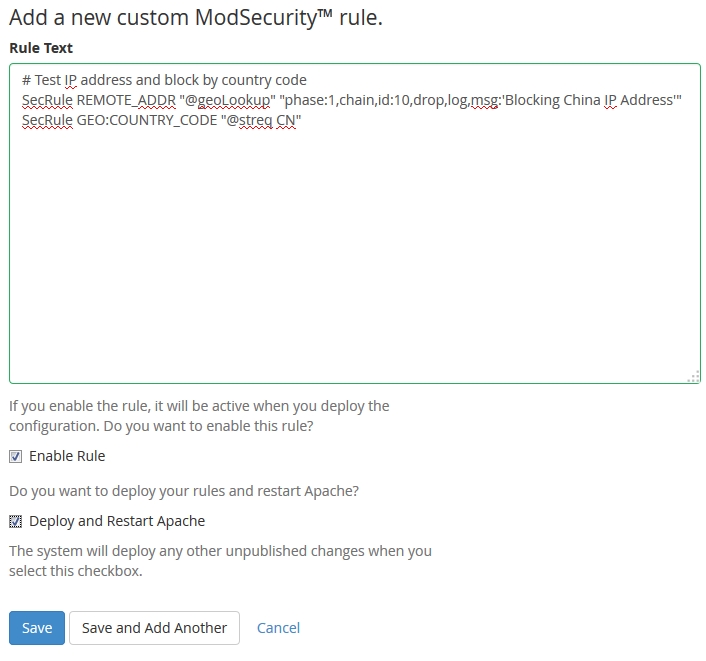
That said if you really want to do this (I\'m telling you, it\'s a bad idea) it\'s covered in the documentation. To fully whitelist a remote address it\'s very similar to the above rule: SecRule REMOTE_ADDR \'123.123.123.123\' 'id:28375,allow\' Generally though I recommend whitelisting broken rules instead. I made cPanel aware in the past that their autodiscover user agent is (was?) libwww-perl which is blocked by many modsec rule sets. I\'m still waiting on an update to case CPANEL-268 for a resolution of this as far as I know.
 I was hoping that was already fixed. If you have log entries from the cpanel autodiscover IP addresses we can figure out why they\'re being blocked. I don\'t use cpanel\'s autodiscover server. My server should be redirecting the request to the exchange server for the proper autodiscover. This is what the log shows: 960015: Request Missing an Accept Header Request: POST /autodiscover/autodiscover.xml Action Description: Warning. Justification: Match of \'pm AppleWebKit Android\' against \'REQUEST_HEADERS:User-Agent\' required. For this type of request I think there was another error that was getting logged.
I was hoping that was already fixed. If you have log entries from the cpanel autodiscover IP addresses we can figure out why they\'re being blocked. I don\'t use cpanel\'s autodiscover server. My server should be redirecting the request to the exchange server for the proper autodiscover. This is what the log shows: 960015: Request Missing an Accept Header Request: POST /autodiscover/autodiscover.xml Action Description: Warning. Justification: Match of \'pm AppleWebKit Android\' against \'REQUEST_HEADERS:User-Agent\' required. For this type of request I think there was another error that was getting logged.

I don\'t have it with me, but each time I see it I use the report option. Not that cPanel ever bothers to look at, much less fix, reported bugs. In addition this is another one that has yet to be fixed in more than a year! 960008: Request Missing a Host Header Source 127.0.0.1 Request: GET /whm-server-status Action Description: Warning. Justification: Operator EQ matched 0 at REQUEST_HEADERS. As with any mechanism that blocks web traffic, there is the risk that the rules could block legitimate traffic (false positives). While both OWASP and cPanel, Inc.
Aim to curate the OWASP rule set to reduce the potential for false positives, there is a risk that the rule set may block legitimate traffic. Review the ModSecurity Tools ( Home >> Security Center >> ModSecurity™ Tools ) interface routinely to evaluate the traffic that the rule set blocks and whether these blocks affect legitimate users.
...'>How To Install Modsecurity In Cpanel Godaddy Login(29.11.2018)How can I host my Django website from Godaddy.com? I doubt if godaddy cpanel has this feature but if you can find modsec manager plugin in your cPanel,.
Sucuri should be filtering most bad traffic. I don\'t recommend whitelisting the IP completely, except maybe in csf.ignore if you are using CSF and LF_MODSEC. That\'s all I would do (add the ip to csf.ignore so it doesn\'t get blocked completely). Reson being, things like cloud firewall or ddos protection are forwarding requests that other people make; it could be forwarding malicious requests along with good ones.
Obviously the point of the sucuri firewall is to filter out the bad ones, but it might miss some. If there\'s one particular rule that the sucuri IP is tripping due to it proxying requests or something, you should just whitelist the rule(s) causing issues.

That said if you really want to do this (I\'m telling you, it\'s a bad idea) it\'s covered in the documentation. To fully whitelist a remote address it\'s very similar to the above rule: SecRule REMOTE_ADDR \'123.123.123.123\' 'id:28375,allow\' Generally though I recommend whitelisting broken rules instead. I made cPanel aware in the past that their autodiscover user agent is (was?) libwww-perl which is blocked by many modsec rule sets. I\'m still waiting on an update to case CPANEL-268 for a resolution of this as far as I know.
 I was hoping that was already fixed. If you have log entries from the cpanel autodiscover IP addresses we can figure out why they\'re being blocked. I don\'t use cpanel\'s autodiscover server. My server should be redirecting the request to the exchange server for the proper autodiscover. This is what the log shows: 960015: Request Missing an Accept Header Request: POST /autodiscover/autodiscover.xml Action Description: Warning. Justification: Match of \'pm AppleWebKit Android\' against \'REQUEST_HEADERS:User-Agent\' required. For this type of request I think there was another error that was getting logged.
I was hoping that was already fixed. If you have log entries from the cpanel autodiscover IP addresses we can figure out why they\'re being blocked. I don\'t use cpanel\'s autodiscover server. My server should be redirecting the request to the exchange server for the proper autodiscover. This is what the log shows: 960015: Request Missing an Accept Header Request: POST /autodiscover/autodiscover.xml Action Description: Warning. Justification: Match of \'pm AppleWebKit Android\' against \'REQUEST_HEADERS:User-Agent\' required. For this type of request I think there was another error that was getting logged.

I don\'t have it with me, but each time I see it I use the report option. Not that cPanel ever bothers to look at, much less fix, reported bugs. In addition this is another one that has yet to be fixed in more than a year! 960008: Request Missing a Host Header Source 127.0.0.1 Request: GET /whm-server-status Action Description: Warning. Justification: Operator EQ matched 0 at REQUEST_HEADERS. As with any mechanism that blocks web traffic, there is the risk that the rules could block legitimate traffic (false positives). While both OWASP and cPanel, Inc.
Aim to curate the OWASP rule set to reduce the potential for false positives, there is a risk that the rule set may block legitimate traffic. Review the ModSecurity Tools ( Home >> Security Center >> ModSecurity™ Tools ) interface routinely to evaluate the traffic that the rule set blocks and whether these blocks affect legitimate users.
...'>How To Install Modsecurity In Cpanel Godaddy Login(29.11.2018)